ID Scanning
Executive Summary
Nametag takes advantage of the powerful capabilities available in modern smartphones to verify your identity. By scanning your government-issued identification and your face, we can validate your identity in seconds. We use optical character recognition (OCR), machine-readable data, machine learning and computer vision to accurately match you to your identity documents. The process is fast and painless thanks to our user-friendly interface. On average, you will complete the verification process in less than 30 seconds.
Scanning Process
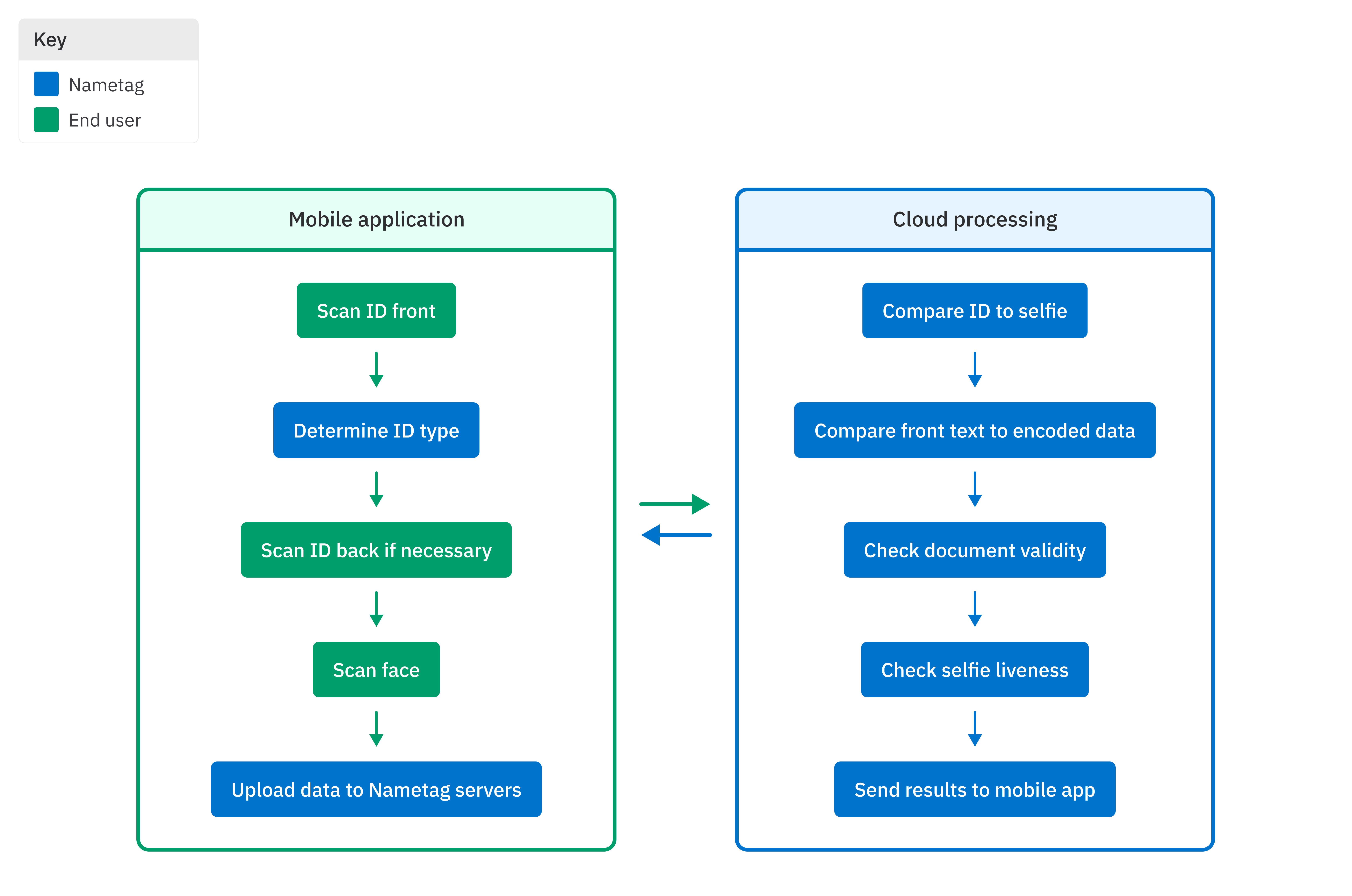
Nametag performs ID verification using the combination of our app on your smartphone and our cloud-based software. Once you’ve received a request to prove your identity, you will take one or more photos of your ID document as well as a photo of your face. We then send those photos to our cloud infrastructure to confirm a match. A diagram of this process is shown below. The remainder of this document describes on-device processing and server side processing in more detail.
On-Device Processing
The smart phone your in hand is a powerful computer with cameras and many other types of sensors. It is capable of performing complex cryptography operations, applying filters to photos, and may be capable of building 3D maps. Nametag takes advantage of your phone’s capabilities to provide a fast and secure scanning experience.
Image Quality Screening
We do the following to ensure we deliver images of high quality to the server:
- Check for blur
- Check the brightness of the image
- Check for glare
These image quality checks are implemented to run on the smart phone’s GPU where possible.
Workflow
When performing any of the on-device processing steps listed below, we generally work to find information and then do quality checking.
Scan ID Front
First we ask you to point your phone’s camera at your ID document. We then look for a “document rectangle”—a rectangular shape in the photo that appears to be a document. Then we check to see if the document rectangle covers a large-enough area of the image. We ensure it meets other required criteria. For example, the document must include a face.
We then perform image quality screening (described below). If the image passes the screening, we upload the image to our servers and move on to the next step in the workflow.
The median time to complete this scan is 9.59 seconds.
Scan ID Back (if applicable)
Depending on the type of document found, we can use additional information on the back of the document to further validate the document. If the type of document found includes this additional information, we prompt you to turn the document over and point the camera at the back of the document. Once the document has been turned over, we perform image quality screening and then start looking for barcodes or QR codes that we know are associated with identity documents. If a barcode or QR code is successfully found and decoded, the decoded information is sent to the server.
The median time to complete this scan is 7.11 seconds.
Scan Face
After the previous steps have been completed, we prompt you to hold your phone up and scan your face with your phone’s selfie camera. We perform image quality screening and check to see if your face is in the frame. If the position of your face in the frame matches specific criteria about position and size, an image is captured and sent to the server. Some phones provide additional information to assist with liveness verification.
The median time to complete this scan is 2.72 seconds.
Server Side Processing
When we process the data that we’ve received from your mobile device, we associate processing results with a “person object”. In the text below we will talk about the process of matching your ID document to your face.
When processing your sensitive identification information, we adhere to relevant information processing laws. When we receive personal information received from customers or end users in Asia, North America or South America will be stored and processed in the United States. When we receive personal information from customers or end users in Europe or Africa it will be stored and processed in Ireland or Germany.
Face Match
We use the front of the ID document and the selfie from the mobile scanning workflow to check to see if the face on the document matches the face in the selfie. If the faces don’t match, the person object is flagged for manual review. The team here at Nametag then analyzes the document images and the selfie images to determine if the face match process was incorrect.
Document Match
We use information found on the front and the back of certain types of ID documents to assess document self-consistency. Using text extracted via OCR from the front of the ID document and any available data decoded from the back of the ID document, we check to see if name, birthdate, ID number, and expiration date match. If the data doesn’t match, we flag the person object for manual review.
Sharing ID Information After Scan Success
After a successful scanning workflow, we create a key pair in the secure enclave of your device. This key pair is used to sign the authorization you give when sharing your data. Our server validates the signature using the public half of that key pair. Your phone’s biometric authentication hardware then acts as a gate to access the private key in the future. This means that only you can authorize sharing your data.
This means that as long as you have your phone and don’t delete our app, you should only need to scan your ID one time. Pretty cool! This also means that if you lose your device, recovering your Nametag, or recovering access to any accounts that use Nametag for login purposes, only requires a quick ID scan. No passwords, no tech support. Extremely cool.
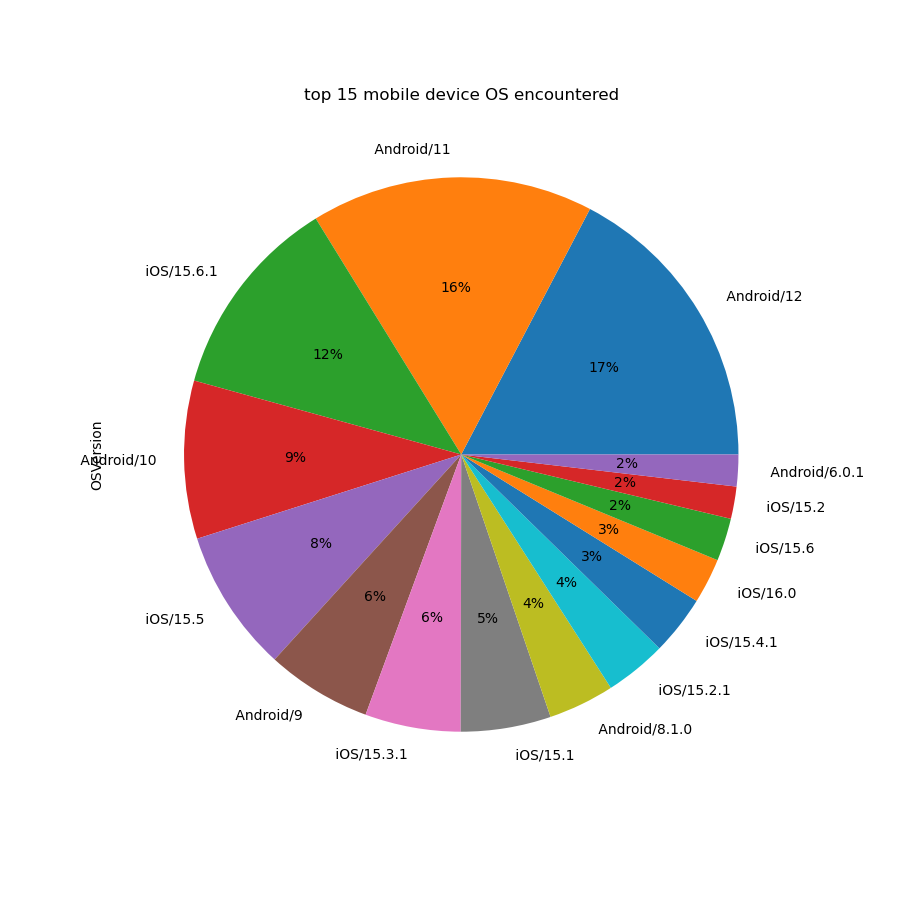
Population Statistics
Out of all scans completed, 49.1% were completed on Android and 50.9% were completed on iOS. Below we show a breakdown of the top 15 mobile operating systems that have used our service.