Amidst the carnage of this year's data breaches and ransomware attacks, one consistent theme has emerged: IT helpdesks are being targeted by attackers using advanced social engineering techniques to trick support agents into unwittingly granting account resets.
In April, the U.S. Department of Health’s Health Sector Cybersecurity Coordination Center (HC3) specifically warned that threat actors are systematically targeting IT helpdesk employees to cripple American healthcare systems.
Several cybersecurity leaders have proposed “visual verification” as the way to stop attackers from convincing your helpdesk to give them access to accounts that are otherwise protected by multi-factor authentication (MFA). Okta’s chief security officer, David Bradbury, said that the way to prevent attackers from gaining this level of access by impersonating an employee or customer is to add “a visual verification step at the helpdesk”.
In this article, we’ll explain what visual verification means, and explore some ways you can add visual verification to your business to stop helpdesk hacks before it’s too late.
.png)
What is Visual Verification?
Visual verification (often referred to as ‘visual identity verification’) is the process of performing a visual inspection of a person’s identity, to ensure that they are indeed who they claim to be, before granting access. This inspection must occur either in person or via a trusted video source. Crucially, visual verification cannot be performed over the phone or in a support chat, Slack or Microsoft Teams conversation, or email thread – it must be performed by a human’s visual inspection or via computer vision. Visual inspection has emerged as an essential method because devices can easily be stolen or lost. The only way to verify someone with certainty is to visually inspect the human themselves.
When to Use Visual Verification
Visual verification can be an effective authentication method for high-risk moments, where basic verification factors can't provide the necessary level of assurance. Use visual verification at the following times:
- Password resets for privileged users
- Multi-factor authentication (MFA) resets
- Access grants (e.g. granting user permissions to view sensitive data)
- Ownership transfers (changing ownership of an account)
- Large transactions (e.g. transferring significant funds)
- Ad-hoc, when someone suspects malfeasance
Visual Verification and Social Engineering
Social engineering attacks involve manipulating people to gain unauthorized access to systems and data. Attackers often impersonate employees, convincing helpdesk personnel to reset passwords (using MFA via an SMS or email that the attacker has already compromised), reset an MFA device (so the hacker can use their own device), or simply grant access to assets, applications, or sensitive information.
This is not a sophisticated attack; the attacker simply finds info about an employee or customer online, calls or messages the customer support team, and impersonates this person in an attempt to steal their account. The problem is that helpdesk and support teams do not have sufficient tools to distinguish these attacks from the real people.
Once the conversation has begun, the attacker claims they’ve lost their multi-factor authentication (MFA) device, typically their mobile phone or a physical security key, and are therefore locked out. They say they need their access to be reset urgently, as they’re losing valuable work time.

Social engineering is hard to detect and can be even harder to stop. Increasingly, attackers are using generative AI to create live video deepfakes, like in the case of the British engineering firm that lost $25 million to hackers who impersonated their CFO. And you can’t expect helpdesk employees to be security and psychology experts.
This is, in part, why Okta’s own Chief Security Officer (CSO) suggests that companies add a visual verification”step at the helpdesk. The idea is basically this: you can’t trust device signatures, traditional multi-factor authentication (MFA), or security questions to guarantee that someone is who they say they are. So, verify their identity visually.
How to Add Visual Verification to Your Helpdesk
Option 1: Zoom calls
One way to do remote visual verification is via video call. It works like this:
- Someone contacts the helpdesk asking to reset their password, saying they lost their MFA device, or requesting access to sensitive company data or systems.
- The helpdesk agent sets up a video call via Zoom, Teams, or some other video conferencing system. Some companies require that the employee’s direct manager join as well. Often, schedule conflicts mean that the call can’t happen for hours or even days.
- Once on video together, the helpdesk agent and employee’s manager can see that the person on the other end is a real human being, that their face matches their employee record, and can ask them questions to verify that they match the account on file.
Clearly, this is extremely complicated and time-consuming. Employees often lose hours or days of productivity; managers have to drop everything and disrupt their workflows to verify their employees; and service agents are wasting time they could spend on other tickets.
No one has yet performed a dedicated study of how long it takes to do visual verification by video call. But it takes 2 to 30 minutes to reset someone’s password, and it seems reasonable to judge that video verification takes a similar amount of time. When you account for the manager’s time and the employee’s lost productivity while waiting for their verification call, the costs of video visual verification are staggering.
What's more, visual verification via Zoom call is not secure. Helpdesk agents will likely not be able to tell the different between a real ID and a fake ID held up in front of a webcam. Additionally, hackers are now using live video deepfakes to impersonate legitimate employees in a way that's virtually impossible for a human to detect.
Thankfully, there’s a way to do automated visual verification.
Option 2: Automate visual verification
The point of visual verification is to prevent social engineering-related helpdesk hacks by verifying that the person contacting the helpdesk really is who they say they are. But doing this via video call is far too slow and time-consuming. This is where Nametag can come in.
Nametag is an identity verification tool built for the helpdesk. It uses AI-powered biometrics and cutting-edge mobile device security to quickly verify the person behind the device. It takes less than 30 seconds, and stops social engineering and account takeovers in their tracks. We surround your IAM and MFA to achieve the high level of assurance needed for admin-level functions like password and MFA resets, and access grants.
Here’s how it works:
- When someone calls the helpdesk, send them a link to verify their identity Nametag. You can text them the link via SMS, or copy it into an email or chat session. Or, they can scan a QR code to initiate self-service secure account recovery.

- Once the employee clicks their link or scans the QR code, it opens a modal on their device (no app download required). They scan a government-issued ID, then take a quick selfie. The system verifies their ID, uses advanced facial biometrics to verify their selfie, and then compares the two.
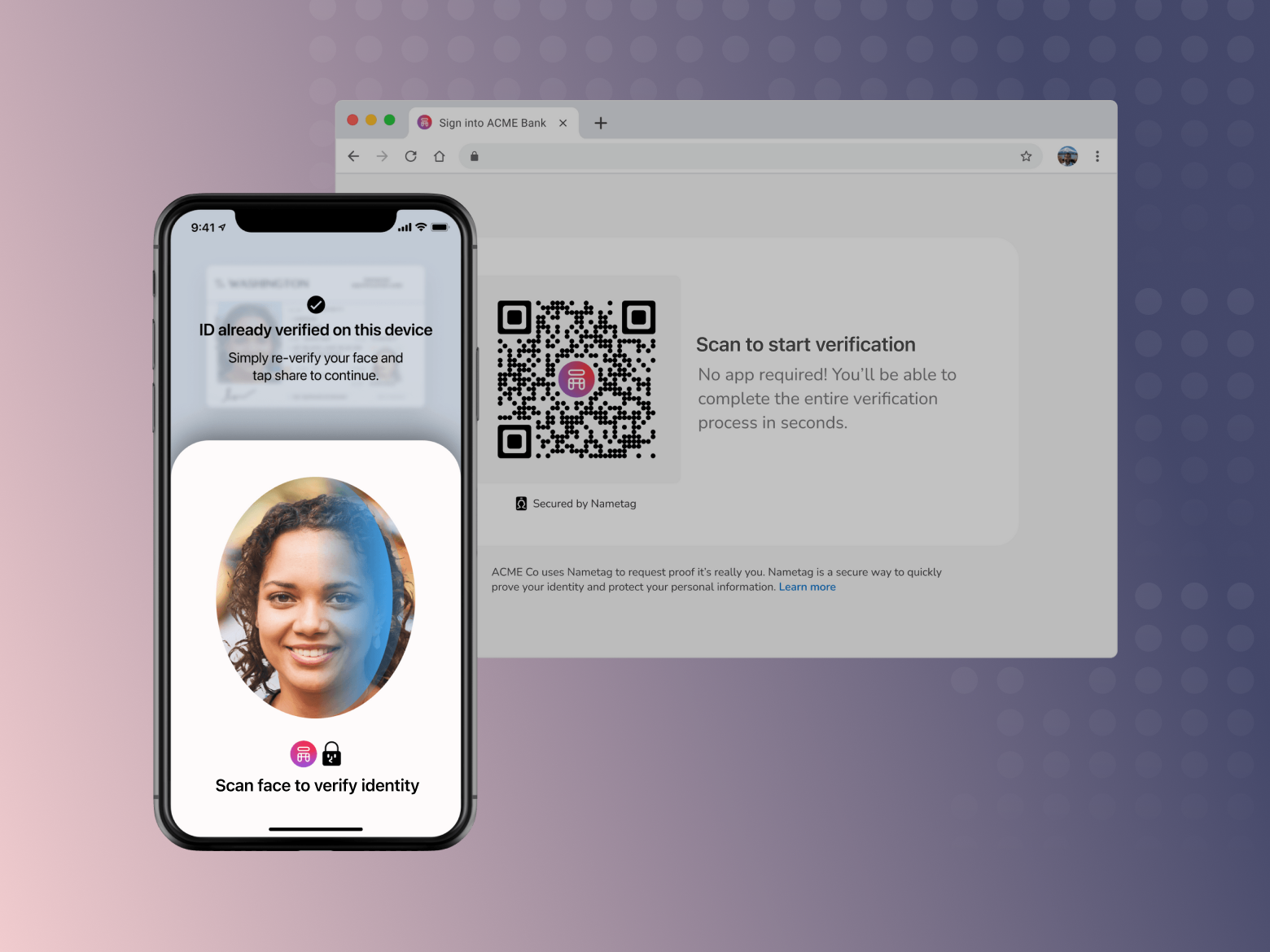
- Once Nametag finishes the verification, your agent console is automatically updated with the results of our analysis. The authentication result is as trustworthy as a video visual verification, in a fraction of the time and with a fraction of the resources required. The helpdesk agent can then proceed with the account recovery, MFA device reset, access grant, or other action.
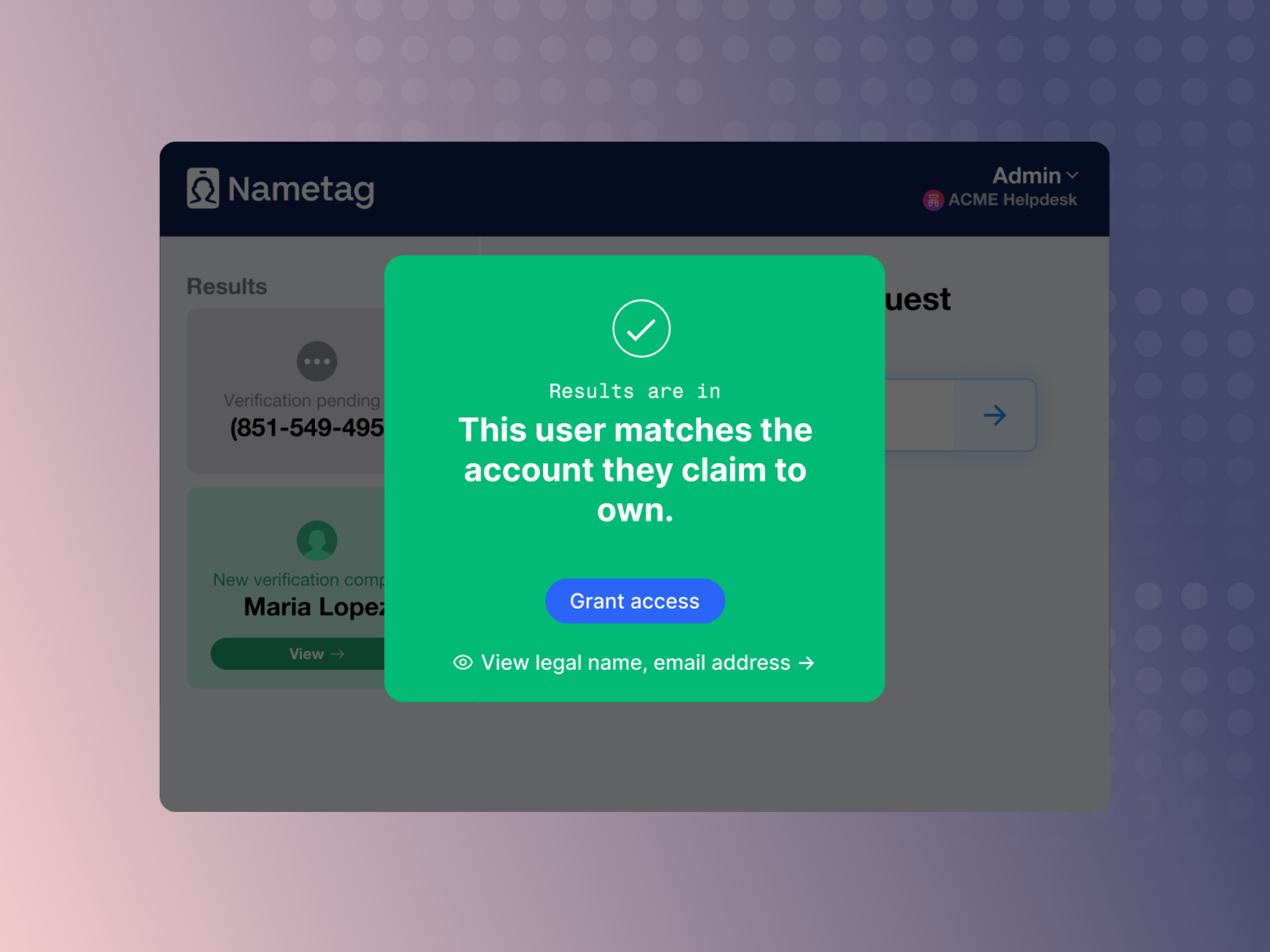
How to Secure Your Helpdesk with Automated Visual Verification
The process for setting up visual verification at the helpdesk can be easy or hard––it depends on how you do it. Doing it by video call uses tools you already have (like Zoom) feels like the easiest route, but is actually incredibly painful in practice. On the other hand, automated solutions like Nametag require limited time to set up (more on that in a moment), are fast in the field, and even more secure.
Step 1: Evaluate Your Security
No matter what route you take, start securing your helpdesk by evaluating your helpdesk security. Any good IT or CISO’s office knows what tools you have for security, but how vulnerable are you to social engineering? Some companies have gone so far as to hire experts to do a “social pentest” on their IT department.
Step 2: Set Up Visual Verification
When even Okta’s CISO is suggesting that all companies implement a visual verification step for high-risk helpdesk functions, you know you should be doing the same. You can do visual verification via video call, or via an automated solution like Nametag. Either way, make sure you’ve clearly documented the tools and processes, as well as when it should be done.
Step 3: Train Your Helpdesk Staff
Educate your helpdesk staff on the importance of verifying employee identities and the proper use of visual verification. Make sure they really understand the threats posed by social engineering attacks, and how to utilize visual verification. You can have the best tools in the world, but they’re useless if no one knows when or how to use them effectively.
Step 4: Monitor and Review
Finally, monitor the effectiveness of your visual verification program. Measure and track how often it’s being used, how long it takes to verify, and other relevant metrics. Remember that staying proactive and continuously improving your security measures is critical in today's fast-moving threat landscape.
Conclusion
Cybersecurity and IT teams are under greater pressures than ever before. The recent wave of attacks targeting security providers just goes to show that no one is safe.
If a company is a castle, the IT helpdesk is the gate: the most vulnerable point. In addition to standard practices like setting up multi-factor authentication and identity and access management (IAM), companies need to implement strong, biometrics-based authentication measures to verify employees contacting the helpdesk. It’s the only way to stop social engineering attacks and prevent help desk hacks.



