Introducing the 2026 Workforce Impersonation Report. Access the report ->




















Most MFA factors verify devices or enrollment. Nametag verifies people. Our workforce-grade Deepfake Defense™ engine verifies the human behind their device, ensuring legitimate access.
Use Nametag as the step-up authentication factor for high-risk scenarios like IAM admin access or when your SIEM detects suspicious user activity.

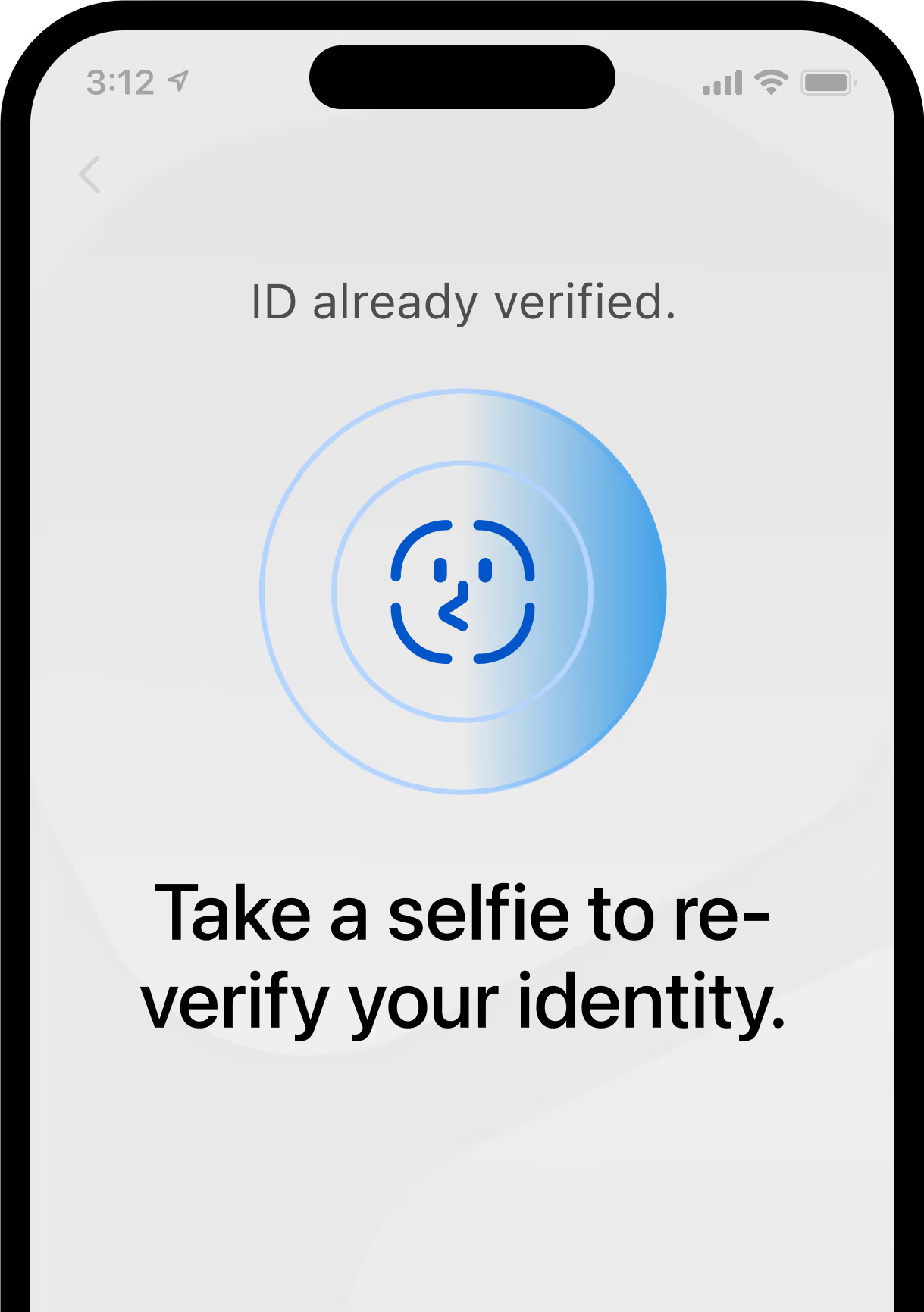
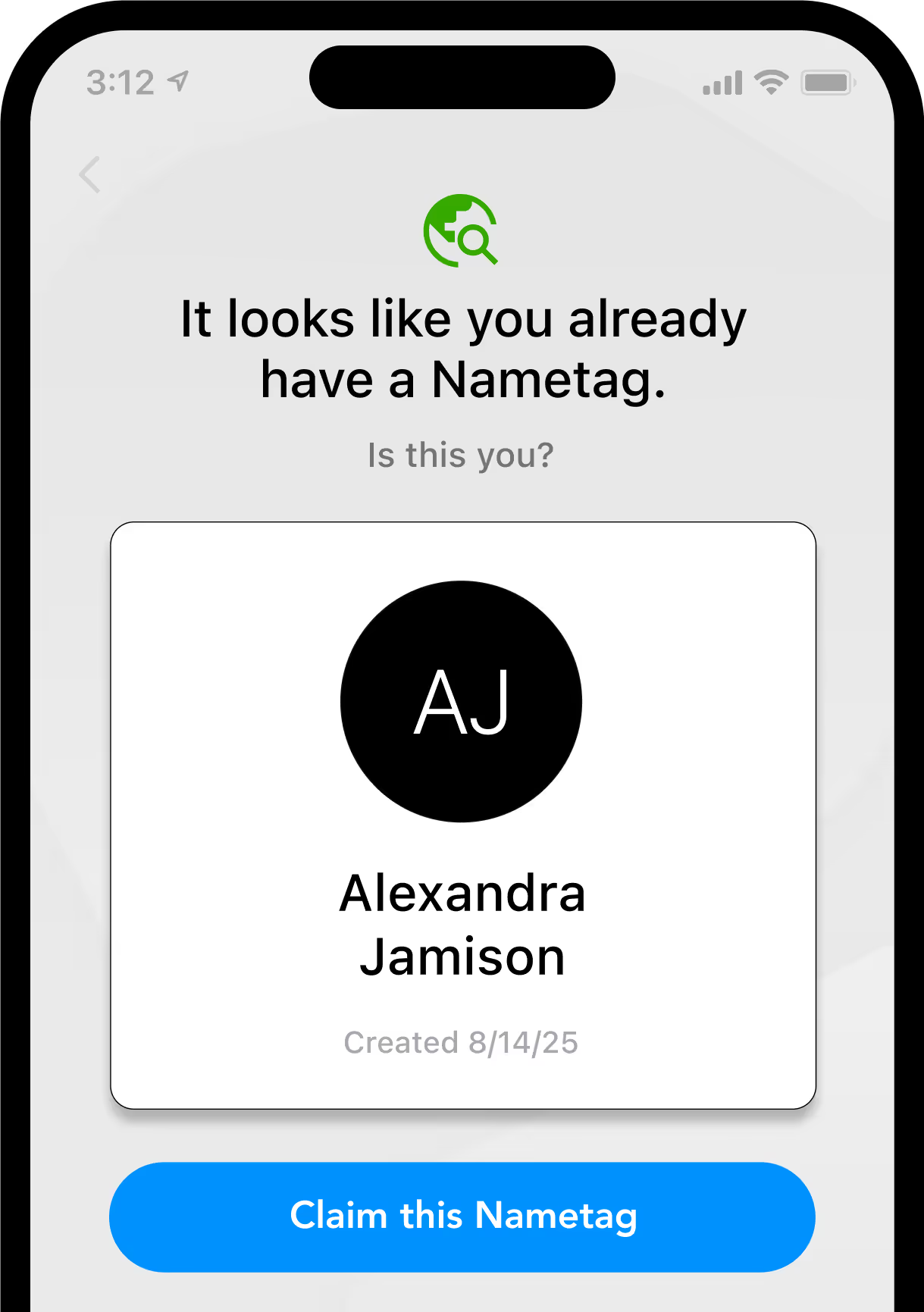


In your mobile app
Use our mobile SDK to create custom, secure step-up authentication flows.

With your IAM & ZTNA
Available as an External Authentication Method for Okta, Microsoft Entra and Cloudflare.





Use Nametag as uniquely secure, flexible step-up authentication factor that can't be lost, stolen, intercepted or phished. Learn more or request a demo today.