How it works
'User is onboarding'

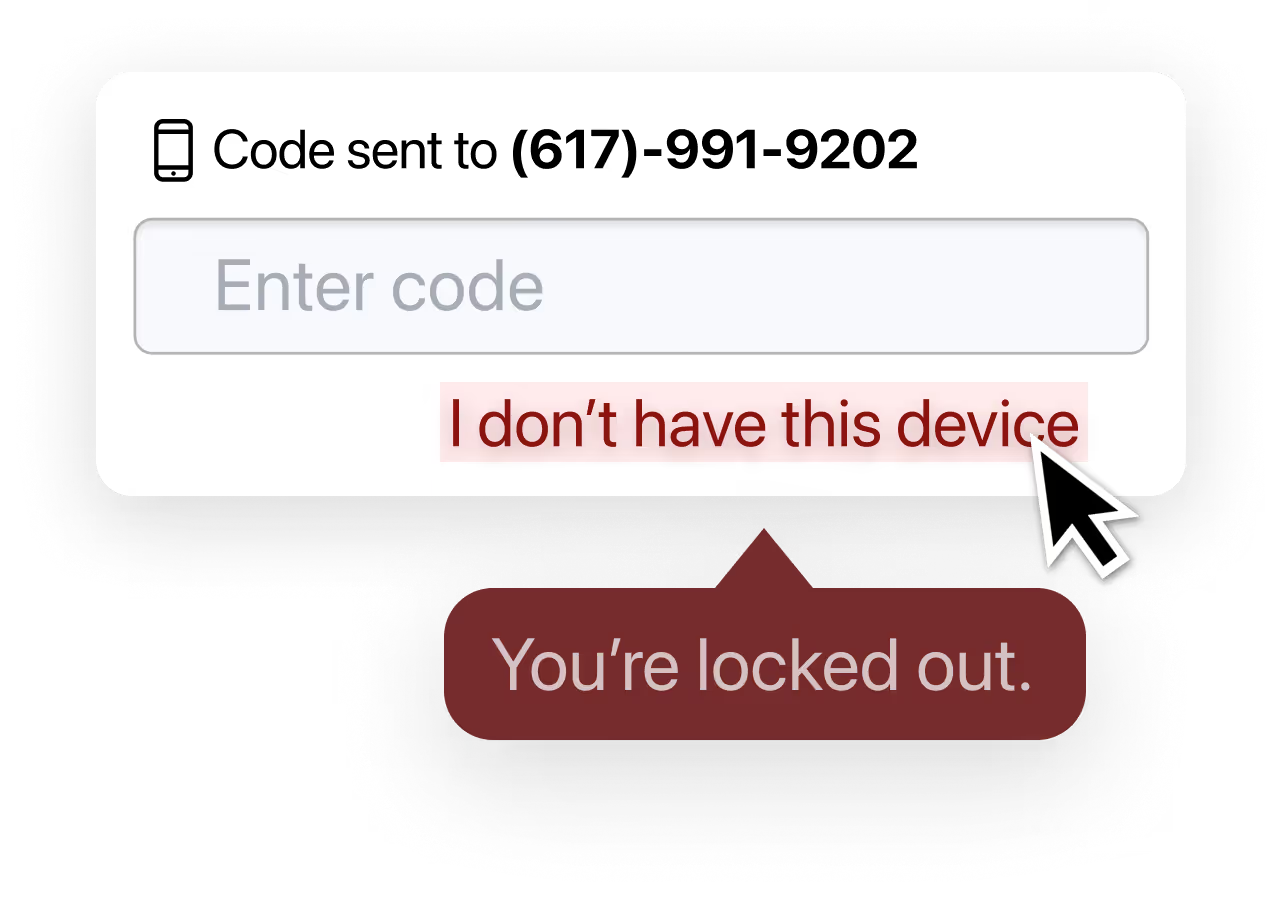
'User is locked out'
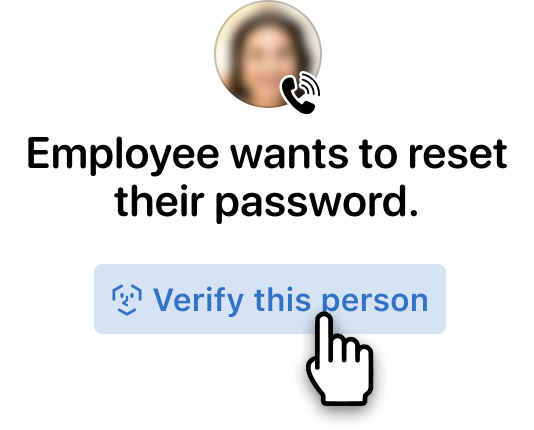
'User calls helpdesk'

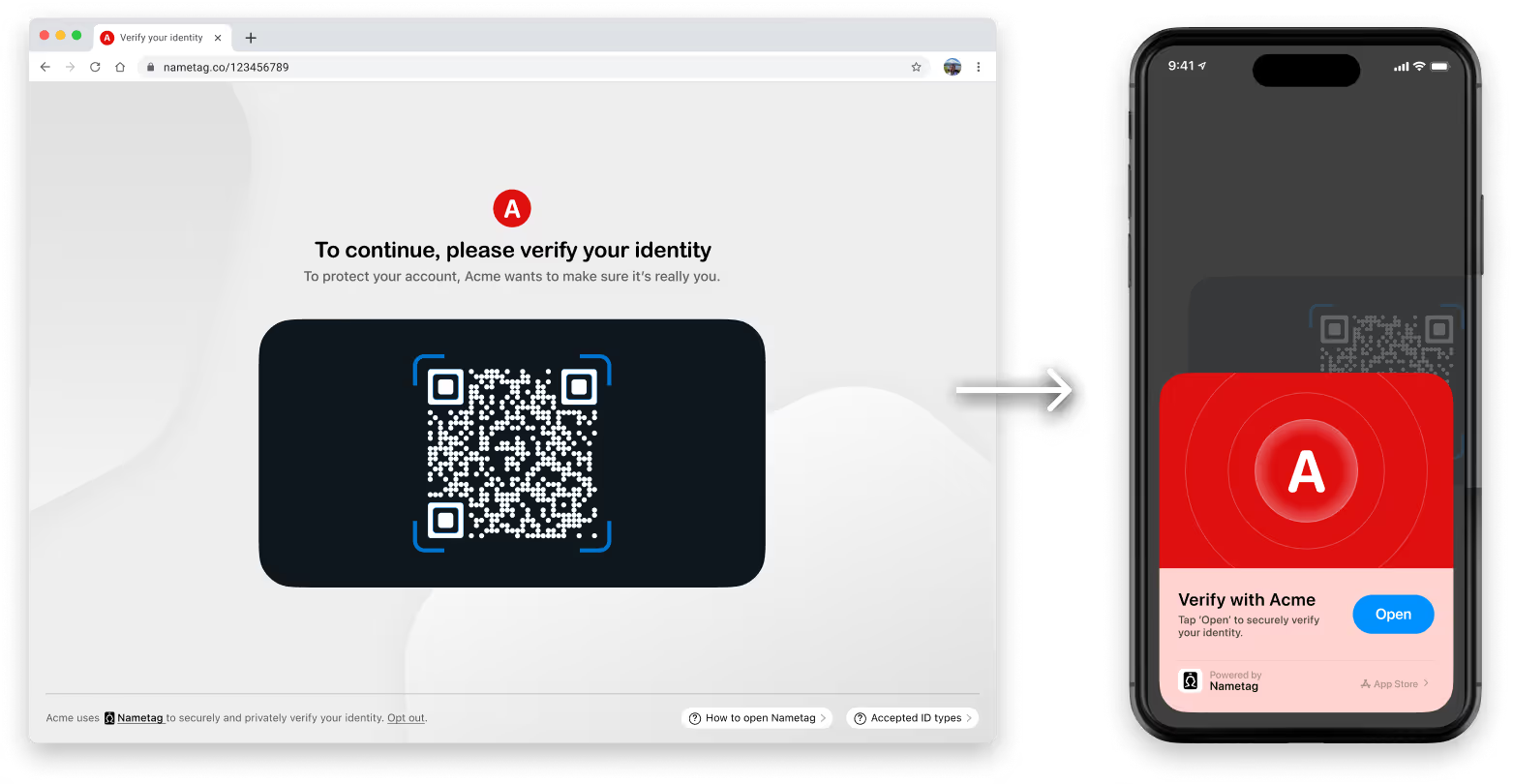
Pivot the person to their mobile device.
Nametag exclusively works on Android and iOS. For security reasons, we do not allow the use of webcams or mobile browsers. To continue, users simply scan a QR code or tap a link.

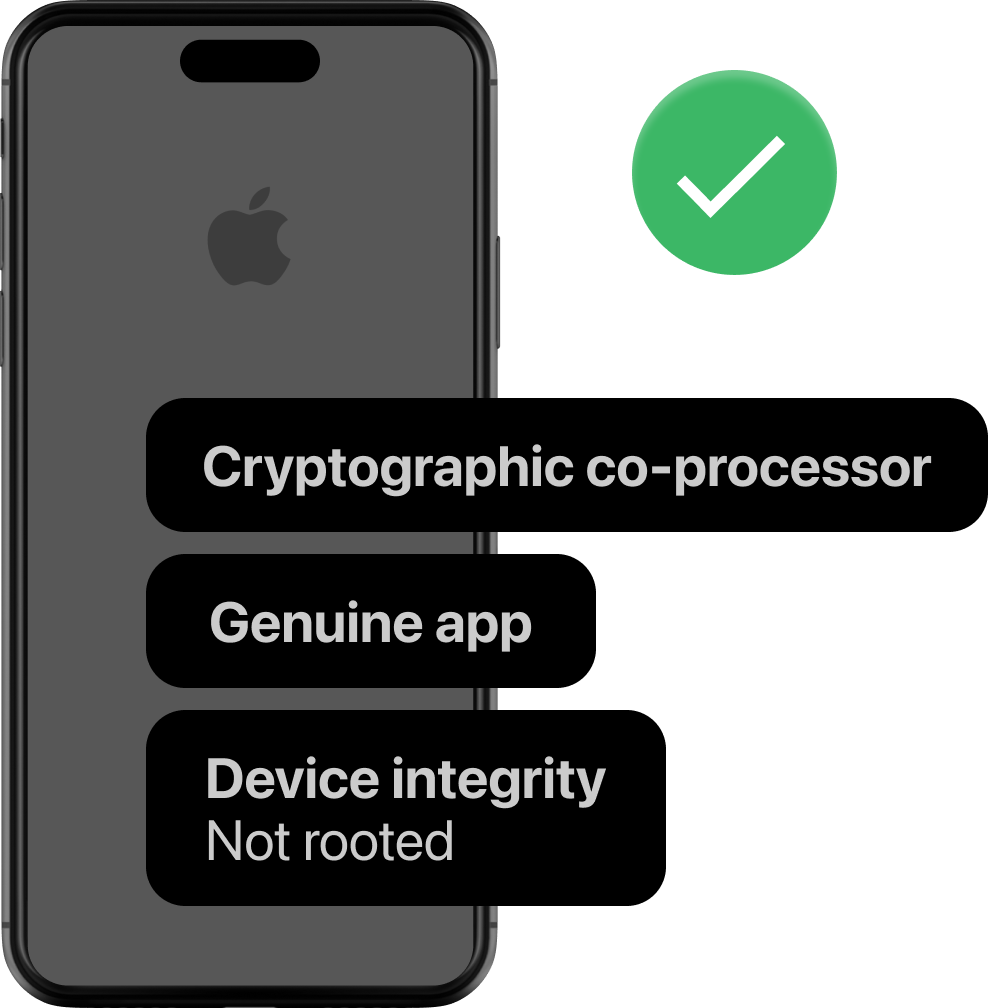
Verify: Is their device trustworthy?
Nametag uses advanced security technology, only available on mobile devices, to ensure that the data we receive comes from the real camera and sensors.

Verify: Are they a human?
Users snap a quick selfie. Spatial Selfie™ technology verifies that they're a real human (not a deepfake, printed photo, or photo held up on another screen).
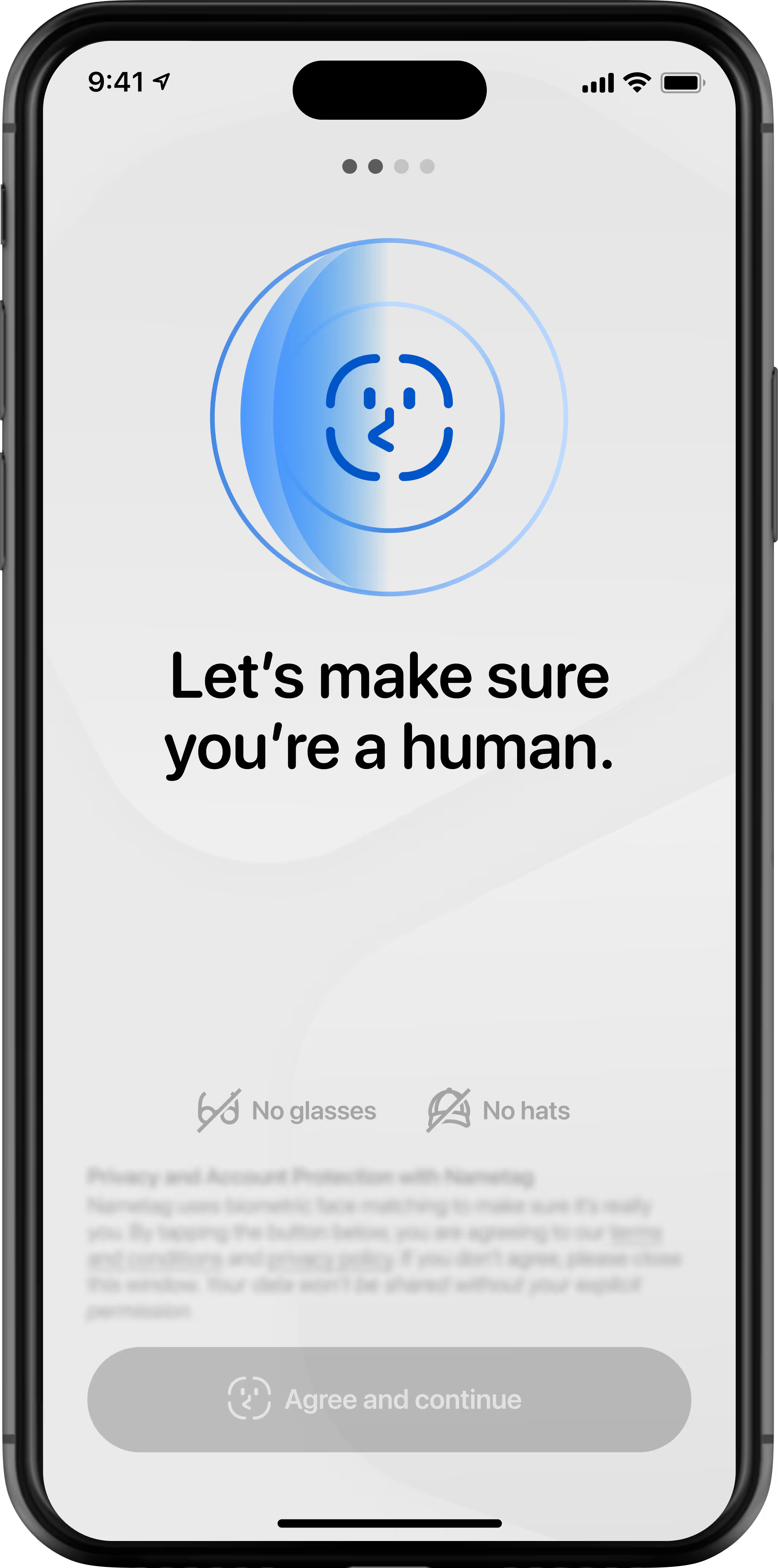


Verify: Which human are they?
Nametag validates their government-issued photo ID or e-ID and compares the photo to their selfie, verifying they're not impersonating someone else.


Match: Are they the right human?
In secure onboarding and self-service account recovery scenarios, Nametag's proprietary technology compares their verified identity to your directories, validating that they're the rightful account owner.

Enroll, recover, or access their account.
Once verified, self-service users can proceed to enroll or reset their credentials. Helpdesk teams see results update in real time in your console, so agents can quickly proceed to resolving user issues.
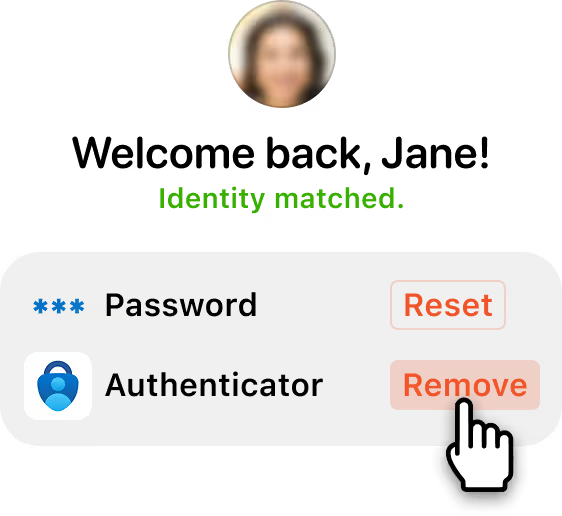

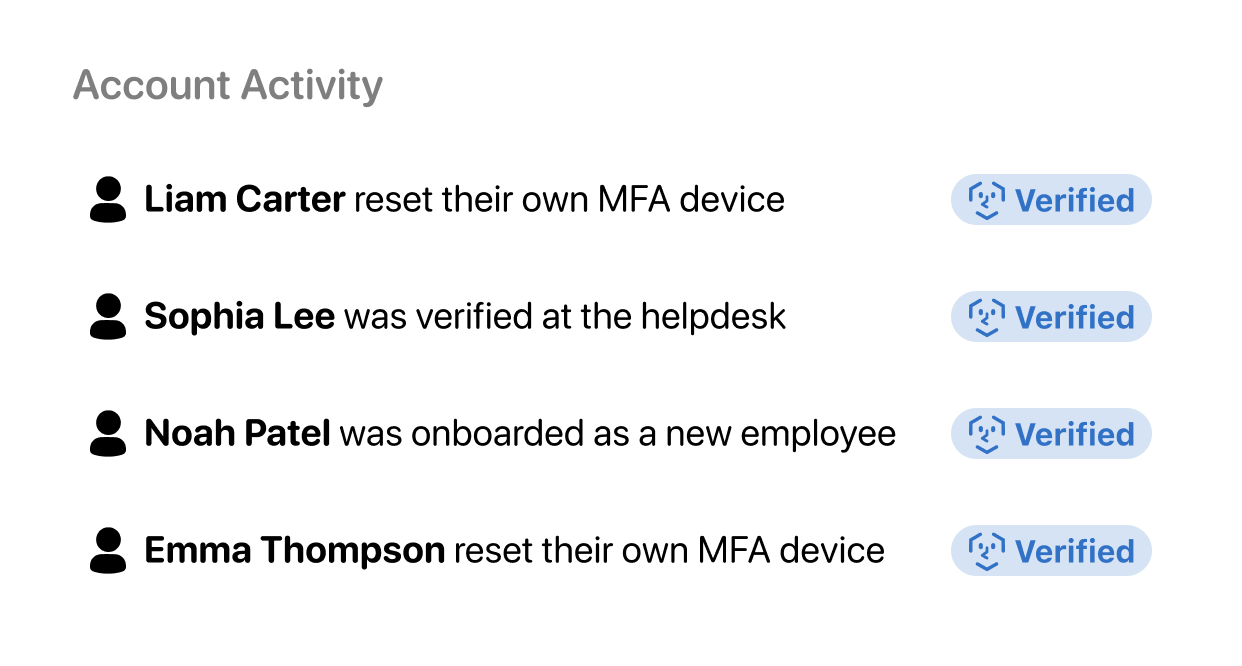
Monitor and review every verification.
Administrators can view and manage verifications and account activity. Auditable verification logs provide full visibility into the decision-making behind every Nametag identity verification.
At any moment of uncertainty, request identity verification.
'User is onboarding'

'User is locked out'

'User calls helpdesk'


Pivot the person to their mobile device.
Nametag exclusively works on Android and iOS. For security reasons, we do not allow the use of webcams or mobile browsers. To continue, users simply scan a QR code or tap a link.



Verify: Is their device still trustworthy?
With every selfie reverification, Nametag reaffirms that the data we are receiving is legitimate, preventing someone from tampering with a device that someone previously used to verify themselves.

Verify: Are they still the same human?
A quick selfie verifies that it's still a real human in front of the camera (not a deepfake, printed photo, or photo held up on another screen).
Nametag's patented technology compares their newest selfie to their prior selfies in a chain which extends back to their verified photo ID document.



Verify: Which human are you?
Nametag validates your government-issued photo ID or e-ID and compares your photo to your selfie, verifying you're not impersonating someone else.


Match: Are they still the right human?
In self-service onboarding and account recovery scenarios, Nametag's proprietary technology compares their verified identity to your directories, validating that they're the rightful account owner.

Enroll, recover, or acess their account.
Once verified, self-service users can proceed to enroll or reset their credentials. Helpdesk agents see results update in real time in our console, so they can quickly proceed to helping the user.



Monitor and review every verification.
Administrators can view and manage verifications and account activity. Auditable verification logs provide full visibility into the decision-making behind every Nametag identity verification.
At any moment of uncertainty, request identity verification.
'User is onboarding'

'User is locked out'

'User calls helpdesk'


Pivot the person to their new device.
Users scan a QR code or tap a link to open Nametag on their phone (no app download required). For security, we do not allow webcams or browsers.



Verify: Is their new device trustworthy?
Nametag ensures that the data and images we receive are legitimate by creating a cryptographic chain of trust all the way down to the hardware level.

Verify: Are they a human?
Users snap a quick selfie. Spatial Selfie™ technology verifies that they're a real human (not a deepfake, printed photo, or photo held up on another screen).



Verify: Which human are they?
Nametag validates their government-issued photo ID or e-ID and compares the photo to their selfie, verifying they're not impersonating someone else.

Seamlessly transfer their verified identity.
Nametag recognizes that the person has verified their identity before, and automatically transitions their reusable verified identity to their new device.
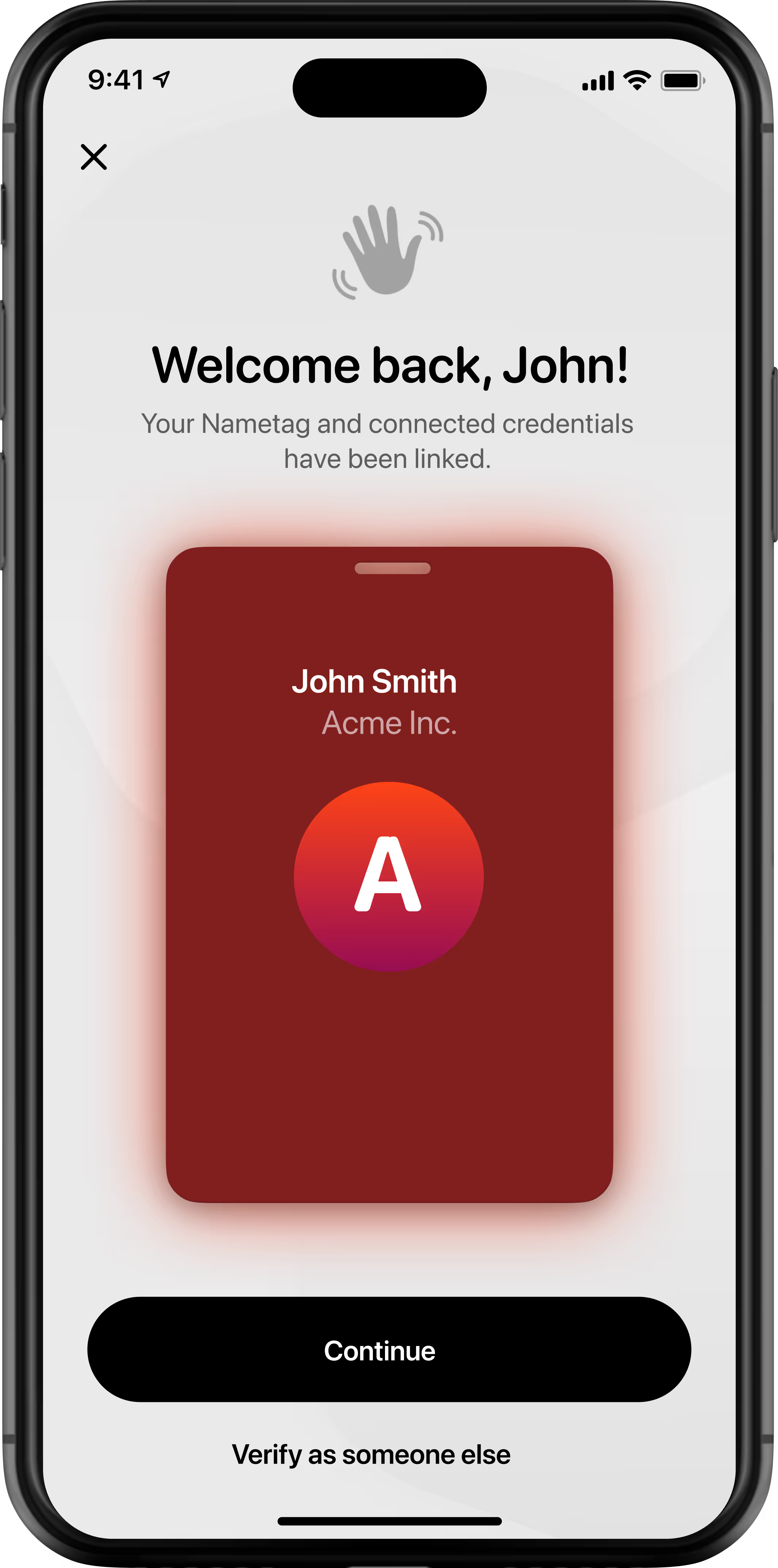

Match: Are they the right human?
In self-service onboarding and account recovery scenarios, Nametag's proprietary technology compares their verified identity to your directories, validating that they're the rightful account owner.



Enroll, recover, or access their account.
Once verified, self-service users can proceed to enroll or reset their credentials. Helpdesk agents see results update in real time in our console, so they can quickly proceed to helping the user.

Monitor and review every verification.
Administrators can view and manage verifications and account activity. Auditable verification logs provide full visibility into the decision-making behind every Nametag identity verification.











